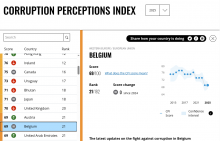
Belgian Corruption Perception is Getting Worse
My favourite corruption story that I tell non-Belgians is the titres-services/dienstencheques racket.
Titres-services/dienstencheques is a kind of money that can be used only for household tasks. Think cleaning lady. At the introduction, they costed ~4.70€/hour to the public while designated organisations cashed in 21€/hour. The gap narrowed later, after creating a few nouveau riches, and after several scandals that were mostly about these people disrupting the office space market with their money.
The subsidy, initially at 16,30€ for every hour worked, came from public money, the stated reason was to draw household workers from the black market, the second reason was to achieve the goal of +100,000 jobs that the then Prime Minister set, the hidden objective was to enrich the few insiders, my memory does not serve me well, but IIRC the party affiliated with public service workers profited the most.